Crypto Security Direct 2022: Everything required to Do for getting Crypto Investment opportunities

Since exemplified from the growing with regard to crypto, it really is becoming trendy to own electronic assets being a hedge towards inflation or even purely pertaining to investment functions. While this is actually a welcomed growth, it does not inform the full history of the additional security obligations that comes with purchasing cryptocurrencies, particularly when you plan upon purchasing holding money.
Thinking about crypto shareholders must bear in mind a long list of variables and try standard security measure measures to make certain they are not encountered with unforeseen hazards. In this help, I will go over all of the security measure measures you must consider as the crypto investor and how to implement them.
What Are Digital Asset Wallets?

Electronic digital assets or perhaps cryptocurrencies are simply just virtual materials powered by simply blockchain technological innovation. The blockchain or passed out ledger details and concurs with the trades executed providing a few digital materials, and in elixir, eliminates the advantages of banks involving third parties. These kinds of currencies you don't have a physical develop. Hence, they might require sophisticated burglar alarms. So , how does one secure a property that technologically does not are present physically together with cannot be trapped in vaults just like cash or perhaps precious metals? The solution is cryptography.
With some cryptography within blockchain technologies, it becomes feasible to give two models of secrets which act as a form of setting up the possession of cash as well as encrypting and decrypting transactions or even information. Known as Private public secrets, these cryptographic keys are usually long guitar strings of alphanumeric characters that will ensure that just authorized organizations have access to cash just like exactly how account titles and security passwords function within the banking globe. Think of it as a method similar to standard banking strategies, where you need to enter the banking account details of the particular recipient confirm the dealings by typing your security password
Proceeding by this example, we can admit private beginning steps-initial share the exact same level of awareness as bank or investment company passwords since they are used to signal transactions and even decrypt typically the incoming finances. On the other hand, consumer keys happen to be blockchain iterations of site names and even numbers, which in turn also encrypt outgoing orders. To efficiently send crypto, you must range from the public key element of the person to encrypt the purchase, and the device must makes use of the corresponding non-public key to decrypt it to obtain the finances.
Nevertheless , unlike conventional banking techniques, it is not a real exchange associated with coins that will defines blockchain transactions. What goes on is that the blockchain only data the exchange of control of money. As such, if you execute deals on the blockchain you are not moving funds.
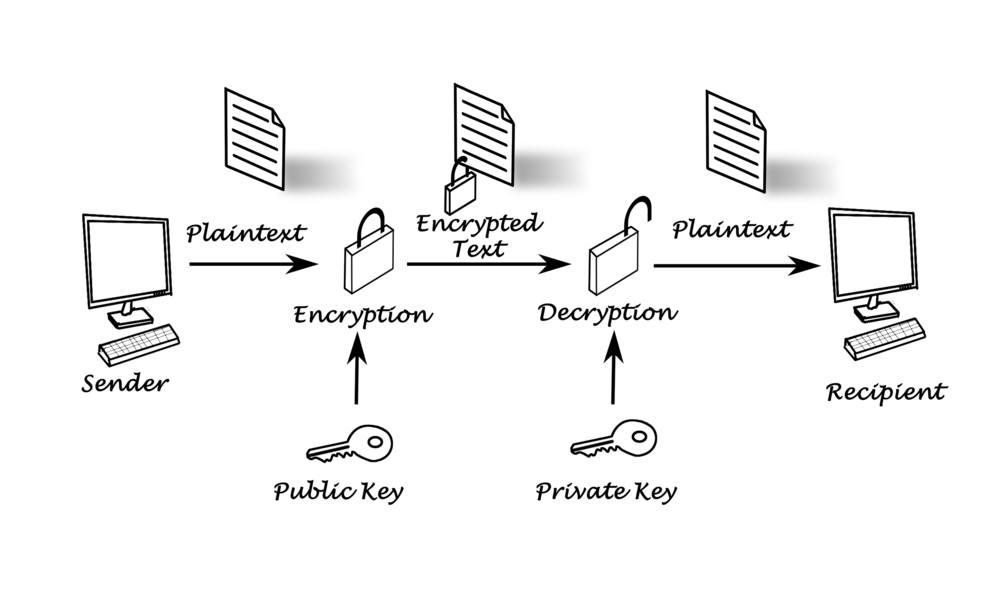
Because of this framework, exclusive and open public keys are crucial components of blockchain security simply because they help conclude the possession of cryptocurrencies and allow users in order to execute purchases. And so, this made feeling to create safety measures infrastructures made to store these types of sensitive important factors. Herein is situated the inspiration for launching cryptocurrency purses.
Consequently , contrary to popular belief, electronic digital wallets never store cryptocurrencies. Instead, they give the appropriate safe-keeping for individual and consumer keys. In addition, note that billfold addresses are merely hashed consumer keys. In other words, wallet includes are reduced versions regarding public practical knowledge. And as featured earlier, cryptocurrency wallets simply alter crypto balances using the change regarding ownership regarding cryptocurrencies. Should you lose access to your individual key, there may be little or no potential for recovering your current coins. In addition, unlike normal financial methods, it is difficult to be able to reverse ventures and even tougher to recover thieved coins. Consequently, you must do any girl to secure your current wallets.
What are Classes regarding Crypto Wallets and handbags?
Given that you understand the basic of crypto wallets, its imperative to research the appropriate security alarm systems. But first, learn about the various lessons of wallets and handbags and the elements that you should take into consideration before choosing one. There exists more than one way to categorise crypto wallets and handbags. You can basic the category on the level regarding autonomy they supply or the mother nature of their on-line to the internet. The previous categorizes wallets and handbags as custodial or noncustodial, while the last mentioned discusses the and wintry wallet category.
Exactly what Custodial together with noncustodial Crypto Wallets?
Certain wallets give full autonomy to consumers by providing associated with the tools they should store his or her private practical knowledge and consumer keys. By doing so, crypto slots have complete control over their own digital property, and maybe they are tasked when using the responsibility involving securing these people. Crypto billfolds that belong to this category can be what we call noncustodial wallets. Could is a granted, there is a second variation, which will stores typically the private tactics on behalf of consumers. The crypto holder has no complete declare over estate assets because they start using a custodial-based approach to wallet service plan.
Custodial Wallets COMPARED TO noncustodial Wallets and handbags
When you compare custodial in addition to noncustodial wallets and handbags, it is not sufficient to just basic your decision on the truth that one gives autonomy the other doesn’t. Although noncustodial iterations regarding digital advantage wallets will be somewhat well-known in the crypto community, they might not match your type of crypto venture. Like quality crypto custodial remedies continue to arise and integrate standard techniques like insurance policy, you might find that it can be safer to clear yourself on the responsibility regarding safeguarding your current private take a moment. Hence, you must take the time to examine the best version of pocket that meets your business or even investment business.
Yet , if we in order to base this specific comparison about present components, it is risk-free to say of which noncustodial wallets and handbags are much more secure compared to the custodial alternative. The moment an individual outsource typically the storage of your respective private key element, then the gold and silver coins linked to your current public residence address are formally not the one you have. Events away from control could cause the long lasting loss of your current crypto groupe.
This particular brings us towards the second category which identifies wallets to be hot or even cold.
What Is A Hot Wallet?
As the name suggests, a High wallet may be a cloud-based electronic digital asset storage area infrastructure that is definitely connected to the net. This jean pocket framework is often available to consumers and facilitates instant financial transactions as the tactics are trapped in the fog up. Also, a lot of variants involving cold billfolds utilize custodial-based infrastructures. Consequently, you have minimal say of what happens to the wallet, in addition to to adhere to typically the policies within the wallet carrier. Note that each and every one software solutions, like desktop billfolds, mobile billfolds, and online wallets belong to this category.
What Are Cold Wallets?
Unlike hot wallets and handbags, cold wallets and handbags allow consumers to store his or her private beginning steps-initial in an real world environment. Consequently, you have to software the pocket book with computer software to implement transactions. As a result of offline dynamics of these pocket book iterations, they give more prevention of hacks or perhaps other dangers on the internet. By natural means, most wintry wallets give you a noncustodial structure. The only conditions are the fresh crop regarding custodial products and services that provide users along with the option of a chilly storage method. The types of wallets and handbags that are plainly referred to as wintry wallets happen to be paper wallets and hardware wallets. These are superior USB generate sticks made to store personal keys off-line.
Cold Wallet VS Hot Wallet
Because of the repeated security hackers associated with fantastic wallets, it is best to opt for ice cold wallets. This way, you eradicate counterpart hazards that may probably cost you typically the entirety of your respective funds. In addition, it reduces the potential of losing the coins as a result of computing inability caused by malware or different malicious program.
non-etheless, these justifications do not take in cold billfolds of their recognizable disadvantage. For starters, it is not made for frequent consumption. In other words, isn't the ideal jean pocket solution for many who are likely to accomplish transactions usually. For this sort of individuals, it really is utilize both equally types of billfolds. I aid that you keep bulk of the funds in a very cold jean pocket while you transport a small percentage into a hot jean pocket for stock trading on deals or running instant financial transactions.
Considerations When Choosing Some sort of Wallet

To get a more thorough article approach handpick the very best digital resource wallets depending on other factors, you should check the top cryptocurrency wallet guidebook on Cryptolinks. Here, I am going to focus on the safety aspect of this particular topic. You need to take into account the subsequent before you select a wallet.
The sort of Cryptocurrency You plan Buying together with Owning
I know that you know nowadays that there are above 6000 cryptocurrencies and bridal party available in typically the crypto industry. And for fresh investors, you should ascertain that your wallet you are thinking about supports typically the crypto you intend to buy. Abiliyy is a very very important factor think about digital billfolds.
The amount of Cryptocurrencies You intend on Acquiring
For anyone interested in ordering more than one endroit, it is crucial to choose whether you wish to have all your current coin within a wallet program or retail outlet them independently. Your decision could determine if you must go for a multicurrency digital advantage wallet or perhaps opt for a distinct wallet for each and every. Also, any time a wallet card issuer promises multicurrency features, you must take the time to homework the effectiveness of the billfold in offering industry-standard to safeguard each reinforced coin.
The quantity of Cryptocurrency and The Form of Crypto Action
A lot more cryptocurrency you are waiting to buy, a lot more it is advisable to check out a broad choice of security implementations. You ought to assess if a custodial or a noncustodial wallet is considered the most suitable. As well, depending on the sort of activities you are waiting to engage throughout, you may have to work with both. Consequently, you ought to distinguish the basic prerequisites of your crypto activities in addition to the security hazards attributed to these people.
Two-Factor Authentication
In addition to the username and password part of safeguards, your jean pocket provider need to include a second layer of which authenticates users’ identity if he or she want to register to the jean pocket, access vulnerable information, or perhaps transfer capital. This next layer involving security is termed the two-factor authentication involving 2-FA. Utilizing this type of system, you could set some sort of biometrics confirmation process an additional security face shield or simply contain the wallet mail and request to achieve OTP computer codes before running certain directions. With this, it is actually less likely to be able to fall recipient to thefts or not authorized access even though your username and password is destroyed.
The particular Reputation of The particular Wallet Service provider
While visiting doubt, the simplest option would be to research the particular wallet provider’s reputation, specifically regarding protection. Things to consider include the breakthrough achieved security-wise, the provider’s level of dedication to protection, the infrastructures provided for users’ safety, and so forth. More importantly, you need to ascertain that this wallet service provider has managed a perfect security report.
Crypto Wallet Security Tips

Here are a few some of the crypto wallet security measure tips you must consider.
Encrypt Your Wallet
Make sure you encrypt your current wallet so that it becomes out of the question for awful actors to pay or copy your gold and silver coins, even when they will breach the principal security system of your respective wallet. The encrypting wallets and handbags is to some extent straightforward to be a majority of wallets and handbags provide built in encryption capabilities for this method. For a computer's wallet, you may want to generate a new passphrase to be able to encrypt your current wallet. In so doing, everyone which includes access for the wallet is fixed to a spectator-only mode. They might track orders but can not execute these people unless they will enter the passphrase. Note that you could have to type the passphrase manually while you want to copy funds.
Also you can encrypt the mobile billfolds. However , not like the process included in encrypting computer's desktop wallets, cell wallets apply pin computer codes for security. Therefore , you merely need to go into a flag to signal transactions.
Backup Your Wallet
Apart from encryption, you may also backup your own wallet just for added prevention of permanent reduction. This safety measures measure is essential because it provides the opportunity associated with recovering exclusive keys in the event you lose your own phone or even computer. In order to backup your own wallet, now you can find inside the wallet application an option to have a seed saying. The seeds phrase can be a list of randomly words, that can be used to recover the lost finances. Once you create the seeds phrase, it is crucial to store this in a protected location. You are able to either record it on paper and maintain it safely or foreign trade it to some dedicated exterior device. You are able to automatically retrieve your finances by stepping into this seeds phrase in to a new finances.
For many who had decided to store his or her seed time period online or perhaps on a product that is coupled to the internet, make sure you encrypt typically the private critical or the seedling phrase. You can even decide to use quite a few locations to stop a single level of malfunction. When you dispense your seedling phrase, your current backup has become less prone to coordinated moves.
Use A Strong Password
As your wallet is really a sensitive profile, you ought to make sure that you use a solid password since the first coating of safety. Ensure that the particular password will be long, distinctive, and distorted. Even, you are able to go so far as to use a security password generator.
Regardless of method you make use of to generate the password, you will need to try as far as possible to remember them. According to type of jean pocket you opt for, you could lose access to your endroit permanently at the time you forget the password. In such a case, it is better to jot down your username and password and keep that in a burial container. This approach is critical for individuals thinking of storing their silver and gold coins in an off the internet wallet for that long time.
Sign Transactions Offline
You are able to capitalize within the strengths associated with both budget frameworks in order to great results. All you need to do is have got offline and online computer systems sharing aspects of a single budget. With this, you are able to store your own private crucial on a cool wallet track actions via the sizzling wallet. In order to issue dealings, you will have to produce a transaction within the internet-enabled pc, transfer this via UNIVERSAL SERIAL BUS to the off-line computer sign this with your personal key. As soon as this is carried out, you will need to deliver the authorized transaction returning to the linked system.
Use Two-Factor Authentication
As stated earlier, 2-FA is a regular security system that individuals expect each wallet in order to provide. The particular unavailability associated with 2-FA limits users to some single coating of security, which is usually easy to link. Also, remember that a majority of finances providers allow 2-FA being an optional safety measures feature. Therefore, the responsibility is upon you to switch on it pick the setting of authentication you prefer.
Use Multi-Signature
The multi-signature or even multi-sig facilities uses a home security alarm that requires several signatures or even private tips to perform critical functions. That way, the multi-sig finances will only verify transactions any time all official users in the account insight their personal keys. To put it simply, a multi-sig wallet enables multiple people or organizations to run just one account. Consequently , all official users of the single finances must insight their personal to exchange funds.
Update Your Software
For those who have a pocket book on your product, it becomes important to redesign the os and other crucial software. This specific practice will make sure that your computer system or mobile phone device is simply not susceptible to hackers. Also, you must the same to your wallet’s computer software. By keeping the software program up to date, you may ascertain you happen to be implementing typically the wallet provider’s latest security and safety upgrades which could defend against fresh security dangers.
Confirm Wallet Addresses
Because it is almost not possible to recover money, it is advisable to double-check recipients’ open public addresses prior to transferring money. This will stop you from sending money to the incorrect address. You may also copy paste address or make use of QR unique codes to restrict the chances of mistakes.
Be Discrete
Another thing many omit to understand is a majority of blockchains do not make sure the anonymity involving users. Alternatively, the system comes with a pseudonymous methodology where typically the identity involving users might be represented by simply aliases or perhaps public the address. Blockchain just like Bitcoin together with Ethereum try a public journal to document transactions and also this framework permits other community participants in order to the activities of each and every address. Consumers lose virtually any form of privateness they considered they have when it becomes practical to url addresses to be able to users’ substantial identities. As a result, it is not aware of post the wallet the address online. This sort of careless act may furnish bad celebrities with all the facts they need to list your crypto activities together with uncover the digital riches. Do not set a aim for on your once again by being uninformed of the hazards lurking online.
If you do not have protected your billfold, it is a terrible idea to maintain your individual keys over a public product. It is also inadvisable to run your current wallet over a shared laptop or computer. You should always start using a private product to access your wallets and handbags. if possible, your could employ a dedicated product for extra protection against not authorized access.
Getting exhausted the particular crypto pocket security debate, the next segment highlights essential crypto swap security recommendations.
What Are Crypto Exchanges?

Crypto exchanges can be platforms offering the center required to vocational, buy or sell cryptocurrencies. It is very challenging to bypass these kinds of entities, specifically if you plan on investment or getting cryptocurrencies. So, it is vital to go over the security hazards associated with these people, knowing totally well that they will be the major cryptocurrency gateway.
So why Do You Need to Take into consideration Security Think about an Change?
Most of crypto deals run a central venture. So, there deliver intermediate expertise by actress as the middlemen that accomplish trades involving users additionally they receive service fees in the form of charge for their challenges. For this technique to work easily, centralized deals must custody of the children users’ solutions. Hence, deals also provide custodial wallets, which will store the privately owned keys for users. Together with judging by typically the recurring security measure crises related to this crypto exchange technique, security is always an integral need when choosing a crypto exchange.

Over time, we have experienced the upsetting effects of employing crypto deals with porous security systems. Involving 2011 and even 2014, Mt. Gox, just about the most dominant Bitcoin exchanges at the moment, suffered a number of security removes, which resulted in the robbery of more than 800, 500 BTC. This particular remains the largest crypto heist in history. Recently, Kucoin lost $240 million well worth of cryptocurrencies to online hackers.
Within hindsight, In my opinion that many from the victims of those incessant assaults would want done points differently, which explains why it is crucial to understand from background. In this area, we will discover the security guidelines that you should consider when using the crypto trade.
Crypto Exchange Security Tips
Carefully Use Exchange’s Hot Budget
Right from details of typically the successful hackers recorded over time, it is clean that assailants majorly give attention to breaching boiling wallets with the obvious causes. Crypto alternate wallets carry pooled tools of consumers and there is ugh such billfolds would go undetected. In essence, consider utilizing Crypto exchange billfolds sparingly to be able to limit your experience of security hazards. For those who simply cannot do those services, they have to allocate a small fraction with their crypto convention to crypto exchange billfolds. The bulk of the funds will need to remain in a chilly wallet.
Use A Strong and Unique Password
A person ought to not use a security password for several exchange company accounts. Ensure that all of your passwords are usually unique strong. This particular precaution removes the risks associated with recording the domino impact. In other words, you no longer need to worry that this porosity of just one of your crypto exchange company accounts will impact the others.
Opt for Two-Factor Authentication
Consider that your crypto exchange gives a secondary part of proper protection in the form of two-factor authentication. Make sure you restrict the activities to be able to exchanges of which support the[desktop] of name verification operations. Check to see of which 2-FA can be described as primary secureness layer designed for all consumers. Note that you could have to set-off it after you create your address.
Choose Advance Cold Wallet Security
Rather for deals to incorporate ice cold storage devices for users’ assets in addition to a majority of the holdings. This method makes it some sort of tad troublesome for online hackers to efficiently hack typically the entirety within the exchange’s property storage technique. As such, typically the assets that happen to be prone to strategies are those trapped in the platform’s hot billfolds. More importantly, deals should circulate assets around multiple fantastic and ice cold wallets to relieve security hazards significantly. It is actually even more extraordinary if the alternate provides insurance policy for consumers. With this, consumers are you can be confident that security measure breaches can be inconsequential for the safety with their funds.
Analyze Data Protection Systems
It isn't just your current asset that may be vulnerable after you utilize a crypto exchange. You need to to be careful of the exchange’s approach to info collection in addition to protection. With respect to the type of crypto trading platform you choose, you might need in order to scale KYC procedures in addition to submit private data starting from your financial details in order to identity paperwork. Just as the particular exchange can be tasked while using responsibility to help keep your cash safe, it should also depart no rock unturned to ensure submitted info does not fall under the wrong arms. On your portion, you should groundwork the platform’s data series and cover policy confirm that the particular exchange is usually competent sufficient to handle users’ data.
Look into the Reputation of Typically the Exchange
The best way to assess the proficiency of a crypto exchange is always to research the historical backdrop. When you do this particular, you can get past safety measures crises noted by the trade and how this resolved this kind of issues. This article help you figure out how committed the particular exchange is always to enable a secure environment designed for users.
Make certain that the Crypto Exchange’s WEBSITE Is Correct
Crypto hackers arrive array of techniques they perform well. One of the popular hoaxes you may face is a web-site cloning layout. Here, hacker clone respectable websites together with lure naive victims to stop their username and passwords. Therefore , acquiring carried away following want to access your crypto wallet. Make perfectly sure that the WEBSITE ADDRESS is correct or perhaps better still, you could bookmark the internet site. The same costs exchange software. Try as far as possible to obtain the official iphone app.
Choose Regulated Exchanges
Certainly, the inflow of crypto exchange polices has reinforced the crypto security anxiety significantly. Change managements happen to be committing even more resources and even manpower to be able to security projects. Platforms happen to be collaborating successfully to stop crypto hackers via carting apart with thieved funds the emergence regarding AML and even KYC regulations is supplying malicious choices something to take into account. Therefore , you must ascertain your exchange is certainly domiciled in the region or perhaps country using strict crypto regulations. To the extent, this could spur typically the exchange to give standard security and safety infrastructures.
Use A Decentralized Exchange
For those that are not at ease with sharing all their private data or perhaps subjecting all their keys to be able to third-parties, you could opt for decentralized exchanges, just like Uniswap, that do not effectively require KYC or custodial-based trades. Which has a decentralized exchange or DEX, you could evade a number of the security hazards peculiar by using centralized deals. You do not need to maintain your solutions on fantastic wallets, neither will you stress about losing the private data to be able to malicious people.
DeFi Security

Talking about decentralized options, they have their own fair share associated with disadvantages. For example, the crypto market documented more hackers in the decentralized finance field last year. The particular growing with regard to open financing has attracted the attention associated with hackers towards the DeFi marketplace. This, along with the nascent nature in the sector, provides exposed customers to a lot more risks, especially rug draw scams.
What Is A Rug Pull Scam?
Area rug pulls are usually coordinated frauds that cash in on the not regulated nature associated with DeFi to produce fraudulent expense opportunities attract unsuspicious victims. Heading by the present system of the particular DeFi scenery, anyone can make a project, punch the DeFi tag onto it, attract traders, and take their money once the financing stage has ended. The security risks posed by this particular scam are definitely more difficult to separate because DeFi promotes the particular animosity associated with developers. Therefore, more often not really, there is no method of catching these types of perpetrators, that is DeFi hackers accounted for over half of the overall crypto safety measures incidents noted in 2020.
Given that DeFi makes offering the most impressive deliver generating prospects, expect typically the sector to remain to attract dubious entities. Consequently, it has become high-risk to invest in DeFi projects while not carrying out the right research together with utilizing a good tools. Learning fully very well that DeFi is an not regulated sector and no way involving recovering shed funds, it can be left to receive investors to continue the extra mile to name viable DeFi investments.
Therefore , you may be wanting to know: How do I avert the noticeable security dangers associated with DeFi? Here is how.
DeFi Security Tips
Opt for Audited DeFi Products
It's not enough to be able to base your quest on prejudiced reviews you get online. In terms of DeFi, it's vital to monetize on the open-source culture within the sector together with analyze the actual codes. Despite the fact that lack typically the technical proficiency to do this, you must ensure that typically the project happens to be audited by simply reputable auditing firms. With an extent, this will help to ascertain of which attackers could not take advantage of pests to steal users’ funds.
State that the Job Has Respectable Backers
Most of top crypto brands need to invest or even integrate along with promising DeFi projects, considering that that it is fast-becoming a viable substitute for conventional monetary systems. Consequently , if you notice that will several founded brands are usually backing the DeFi task, it might show that the task is not operate by unknown entities which there is a operating product.
Look for Liquidity Securing Implementations
It really is imperative limit your DeFi investment actions to methods or tasks that consent to implement fluid locks for that DEX swimming pools. Liquidity hair make it difficult for price providers or task teams in order to withdraw possibly liquidity bridal party or the bridal party allocated to creators before the predefined period. This protection measure makes sure that investors are certainly not susceptible to area rug pulls. Additionally, it shows the particular project team’s commitment towards the long-term durability of the process.
Consider DeFi Insurance
DeFi insurance is definitely an emerging strategy that encapsulates the supply of insurance policy services in order to DeFi customers. With this, buyers can relax knowing that failures due to unexpected security weaknesses can be said. That said, idea is still within the experimental period as there are zero industry-wide criteria introduced however. However , you should look at exploring the choices that DeFi insurance gives in the meantime in addition to check if its compelling sufficient for you.
Stick to Established Projects
Most likely, you will best sticking to analyzed and trustworthy DeFi remedies. These methods have shown outside of a reasonable uncertainty that they present viable and even security-conscious goods. Therefore , as opposed to gamble over the unknown, you might limit you to established jobs.
CONCLUSION
Never forget that the security measure of your comit� and crypto investments is without a doubt nonnegotiable. Even though you utilize these security measure measures, as well ensure that your companies are also undertaking their aspect. Note that you could replicate lots of the security tips and hints highlighted through this guide to receive other crypto investment styles.

